Hello for whoever read this,
My new post will be in blog.mochtar.net , see you in my new blog site.
Read – Write – Execute
Hello for whoever read this,
My new post will be in blog.mochtar.net , see you in my new blog site.
We often use HAProxy when deploying zimbra in large environment for load balancing traffic espesially in MTA services port 25, 465 and 587. but using default configuration in haproxy and zimbra affecting sender IP will be read as HAProxy server’s IP, so we cannot trace email by it’s origin IP. this is a big issue when dealing with spammer either from outside or internal.
Luckily there are option in postfix for read original IP from traffic that was sent by haproxy. the configuration are postscreen_upstream_proxy_protocol (if using postscreen as it’s a default in smtp port 25 since zimbra 8.7) and smtpd_upstream_proxy_protocol then from haproxy side by adding send-proxy option.
So here’s the steps for configuring it:
Continue reading “Using HAPROXY Against Zimbra MTA Services, reveal origin IP”
In ClearOS We can set Ldap service listen to all interface by setting Publish Policy option to All Networks, but maybe for security concern the service was not for ldap but ldaps (SSL ldap protocol) which listen in port 636.
Because there is an application that will be using ClearOS ldap as authentication backend cannot using ldaps (as it’s been hardcoded from vendor) so we need to force ldap (port 389) service to listen in all IP.
So here’s the steps.
vi /etc/init.d/slapd
for ip in $AUTOMAGIC_LANIPS; do
harg="$harg ldap://$ip"
done
service slapd restart
vi /etc/yum.conf
exclude=openldap-servers
netstat -tnap | grep LISTEN | grep 389
Some of our Zimbra customers are complaining for authenticated user can customizing FROM header which can lead to fraud email. this issue can be reproduce by using thunderbird once compose an email as following picture.

or by using this script, change variables username, password, fake_from and to_addr based on your environment.
I created customized milter engine using python milter library for my workaroud with following features:
Continue reading “[ZIMBRA] Prevent User Customizing “FROM” header”
For example you want to fetch all task list which has branch in it as this picture.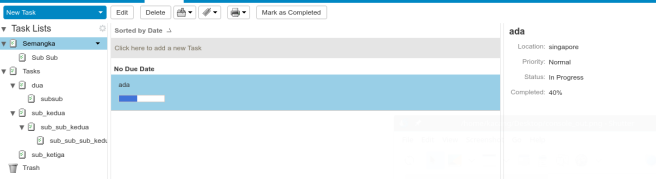
You can fetch them using soap call Search for filter recursively task folder from root dir (/) and GetFolder for fetch task detail, here’s the example script of using mentioned soap call.
First install development package for compiling latest pscyopg2 package.
Note: make sure the version of postgresql server that will be remote using pgAdmin4 is 9.0 above.
sudo apt-get install python-dev postgresql-server-dev-9.5
Continue reading “Installing pgAdmin4 (desktop mode) in Ubuntu”
Sometime our customer that use Zimbra has frequent issue in internal spammer because weakness in user password so i created a script to scanning it then we can push the user to use the hard one. maybe it’s quite similar as my previous post
I made script to make mailman3 installation easy (automated) based on my experience installing it manually. for installation guide and prerequisite condition you can see in it’s repository here https://github.com/iomarmochtar/mailman3_ei
Here’s the post installation topics that may you need:
if you have similar needs for using django template outside django project then this snipped will be useful.
| import django | |
| from django.template import Template, Context | |
| from django.conf import settings | |
| # optional if you just render str instead of template file | |
| from django.template.loader import get_template | |
| settings.configure(TEMPLATES=[{ | |
| 'BACKEND': 'django.template.backends.django.DjangoTemplates', | |
| # if you want to render using template file | |
| 'DIRS': ['/tmp/template_dirs'] | |
| }]) | |
| django.setup() | |
| # variables that will be passed to template | |
| vars = {'name':'mochtar'} | |
| print Template("Using string = {{name}}").render(Context(vars)) | |
| # file say_hello.tmpl located in folder /tmp/template_dirs as it's configured above | |
| print get_template("say_hello.tmpl").render(vars) |
As my previous post about enhancing password policy in ClearOS i mentioned about create simple PHP script for detecting user which using weak password. so i’d like to share it.